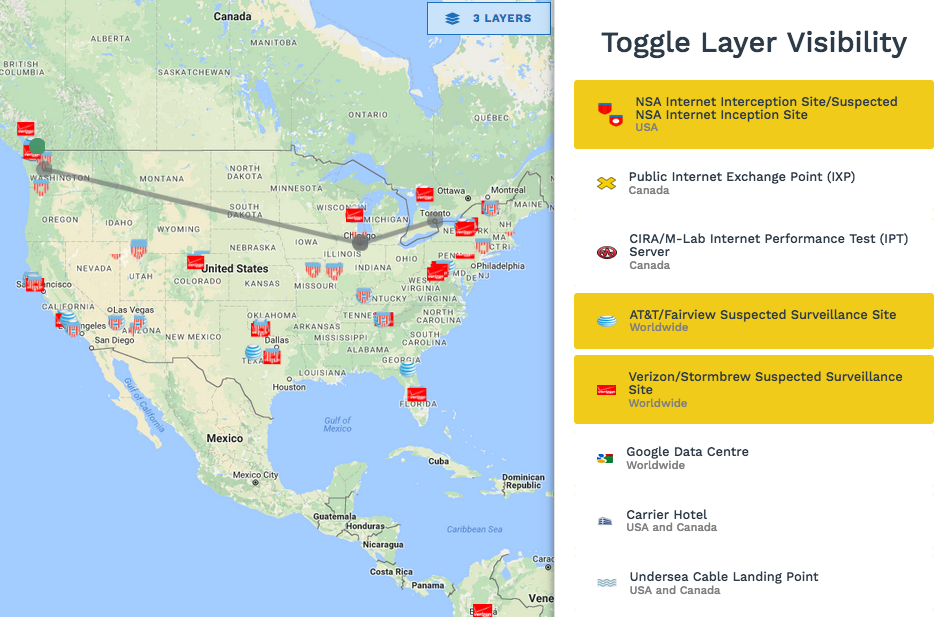
Go to the Map, where you will see recent traceroutes from nearest your location. You can click on the dots and lines to learn more about the route and who carries your data.
To see other routes from near you:
- Click in the From box, to show the menu choices
- Select your ISP, City or Country, or a combination of these, entering the relevant information.
- Click Search.
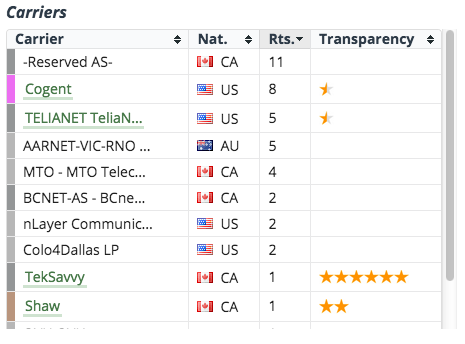
You will see mapped the most recent route that meets these conditions. On the right is the number of routes found and brief details about them. You can map these other routes by clicking on their TR ID number. Below the traceroute information, is the Carriers table with summary information about the various ISPs or carriers that handle the mapped route(s).
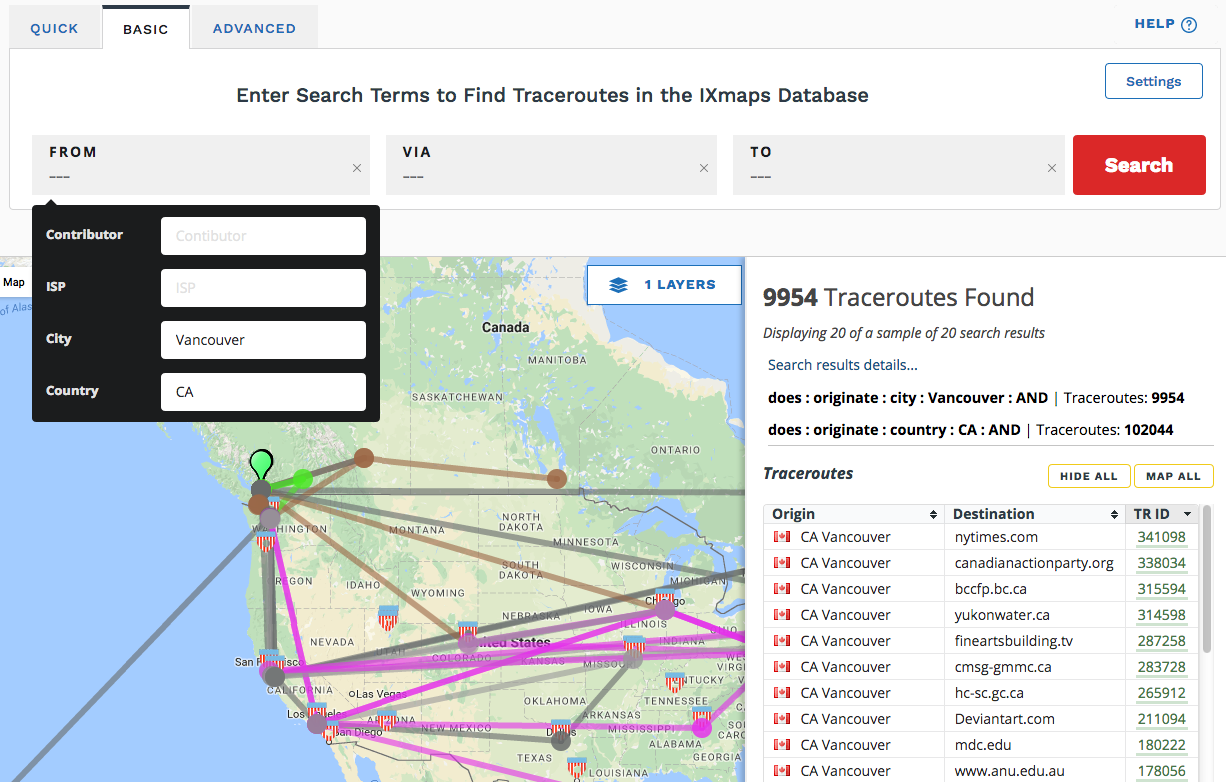
You can refine your selection using From, Via and To.
To see routes from your own personal device, you must first generate them yourself. Go to the Contribute page for instructions on how to do this.
For more details on how to select routes to display, see the Help button on the upper right of the Map page.
See FAQs: